Bookmark Sync Security - Comprehensive Browser List
Overview of various browser sync security systems with a focus on End-to-End Encryption (E2EE) like systems for synced user data such as bookmarks, browser history, and passwords
Disclaimers:
1. This list of browsers is in order of popularity, not most secure, we chose this order to reflect relevance rather than our opinion of which is more secure.
2. This is a breakdown of our findings from reading browser documentation and trying out browser sync and security features first-hand.
3. We have personally audited each browser on this list for claims and features, but haven't gone into extensive depth, such as the use verification of encrypted data.
4. We do not accept or allow sponsors or advertisers on this site and we tried to approach this topic as unbiased as possible.
Browser sync security refers to the measures taken to protect browser sync data (bookmarks, history, passwords, tabs, etc...) that is synchronized across different devices using a web browser. One critical aspect of this security is whether the sync system uses end-to-end encryption (E2EE), a highly distinguished data protection pattern revered for its ability to protect data from surveillance and data breaches. It does this by ensuring that data is encrypted on the user’s device, then sent through the sync servers while in an encrypted state which the servers cannot decrypt, and can only be decrypted by the user. A crucial aspect of an E2EE system is that the data encryption key and passphrase never leave your devices. This protects the data from being accessed by third parties, including the browser sync systems, cloud services, internet service providers, and hackers potentially looking to see or sell information about you on the dark web.
One big distinguishing factor behind considering if a browser sync system has E2EE is if they claim that they cannot "see" your data. It's also important that they specifically mention bookmarks, browser history, and passwords as data points being encrypted, otherwise it could be only the passwords from the password manager that are being encrypted, leaving highly private things like bookmarks exposed.
Not all browsers refer to their encryption systems as E2EE, some may call it client-side encryption (CSE), or simply refer to it as encrypted, which could actually mean all sorts of design patterns with varying degrees of security. The lack of clarity on this topic begs regulation and standardization, particularly regarding how organizations use terminology when referring to encryption systems and privacy.
For example, CSE is sometimes used to imply that passphrases or keys may be sent to the server for server-side data processing, either momentarily or permanently. This is not good for security and it’s totally unnecessary for a sync system. Sync systems are a perfect use-case for E2EE and there should be no compromise. Some of the variations we see in documentation talking about encryption systems come down to subtle differences in technical interpretations of the meaning of E2EE or CSE. Awareness about the technology, and the age of the term (the earliest mention being in 2003) also impact how this topic is communicated. Ideally, browsers make reference to their sync security with correct terminology and define their systems as either E2EE or CSE for clarity and user safety.
If the browser offers encryption at rest or in transit, this does not qualify it as E2EE and is not considered adequate security for highly private user data such as passwords, bookmarks, and browser history. The ability to set a non-recoverable, device-level key/password/passphrase is one of the absolute minimum requirements to fulfill the needs of an adequately private sync security system.
Before we get started going through the list of browsers, if you’re planning on enabling E2EE, remember that your custom passphrase or cryptographic key (sometimes referred to as a primary key or recovery key) cannot be recovered if lost. It is super important to keep a backup of your passphrase or key, ideally with redundancy. E2EE or CSE passphrases/passwords/keys cannot be recovered like account passwords using “forgot my password” features. E2EE passphrases absolutely need to be strong in order to provide adequate data security. If there’s a data breach, brute-forcing your passphrase could be the next option for a hacker, and a strong passphrase can make that practically impossible. Keeping a safe backup can be done in a variety of ways and redundancy should be implemented.
Now let's get to the bottom of this, what popular browsers have E2EE equivalent encryption systems and how do they describe their security and privacy?
Our list is ordered by browser popularity with details about their sync security, and if they make the cut for what we consider E2EE equivalent.
Feel free to jump to the browser of your choice:
![]()
Google Chrome
✓ Chrome has E2EE if you set up your own sync passphrase, but there could be more clarity in their documentation about their encryption system.
Chrome claims to offer sync privacy with on-device encryption using on-device keys that are not sent or stored on Google. This essentially qualifies as an E2EE system without calling it that directly. It is not turned on by default though, in the default state your data is encrypted using your Google account in a method that is not very clearly talked about, but this does not seem to qualify it as E2EE. When a custom sync passphrase is turned on, Google claims in its documentation that bookmarks, history, passwords, and some other sync data are encrypted on the user’s device and can only be decrypted with the passphrase provided which never leaves the user's device. This pretty safely meets the criteria of an E2EE system despite them not directly claiming it. It is important to note that Google does not encrypt your payment methods and addresses from Google Pay with your E2EE passphrase.
Important takeaways:
- With a passphrase, you can use Google's cloud to store and sync your Chrome data without letting Google read it.
- Your payment methods and addresses from Google Pay aren't encrypted by a passphrase.
- Your synced data is always protected in-transit with encryption.
- Unlike most browsers, Chrome lets you set your own personalized encryption passphrase.
What could be improved:
- Chrome could be more clear about if the sync system is in fact encrypting your bookmarks and history specifically with your custom passphrase. They never say it directly but it appears to be implied when mentioning that all sync data will be encrypted. What we couldn't figure out was, if your sync data is encrypted with the custom passphrase or with your account password that is encrypted with your custom passphrase. That slight difference has an impact on the quality of the security system and knowing exactly how it works would be better.
- Chrome should directly reference if their sync encryption system has end-to-end encryption for added clarity, much like how the Safari and Duck-Duck-Go browser currently does.
Here are the steps required to turn on an E2EE-like system in Chrome:
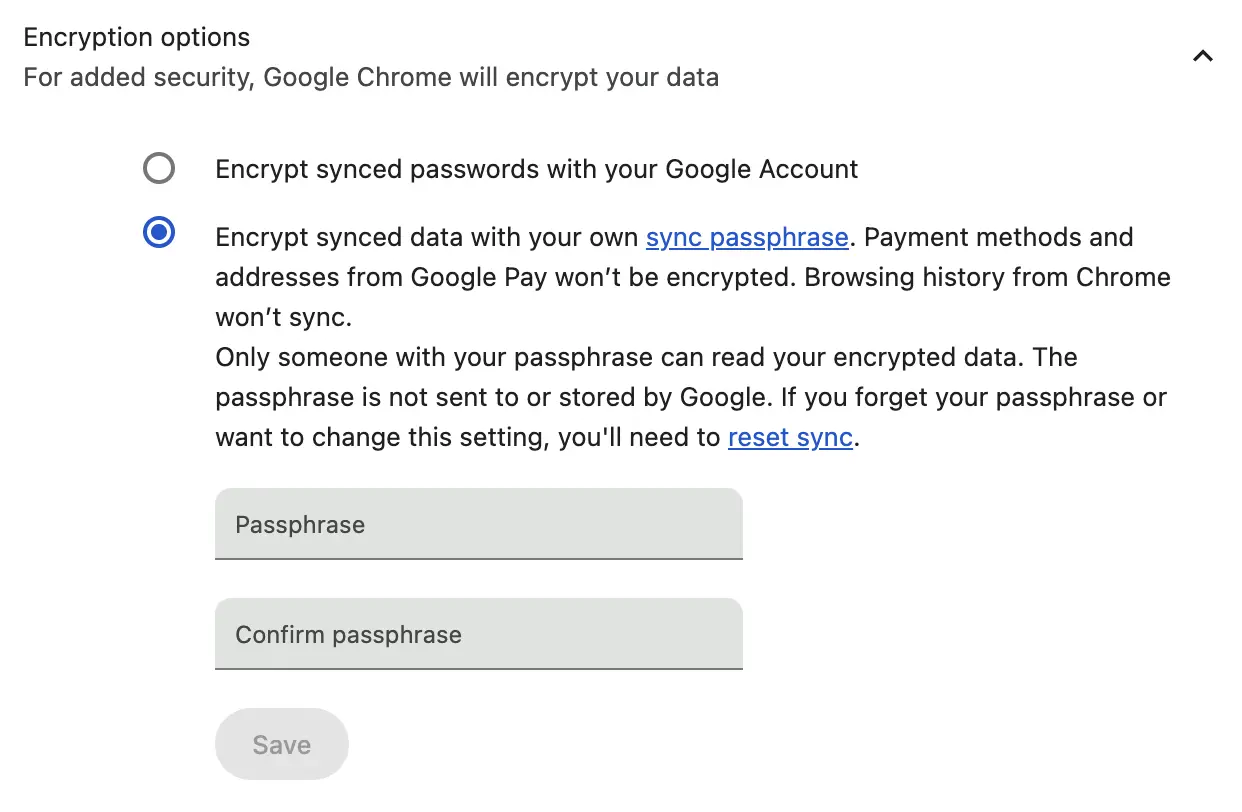
- Navigate to the browser settings.
- Click on the section called “You and Google”.
- Click “Sync and Google services”.
- Under the Sync heading, you should find an option called “Encryption options” that can be expanded.
- Then click “Encrypt data with your own passphrase”, fill out a custom passphrase, and click save.
More from Google:
Sync Management Features:
Note: Mainstream browsers store bookmarks on your computer's hard drive in plaintext. This means they are completely accessible (without the need of special privileges) to other applications on your computer. This is true even if your browser is closed and you're logged out of your browser profile. The rationale behind doing this is to facilitate the import/export wizard that transfers bookmarks between browsers, but it comes at great cost. It opens the possibility for a very serious data breach if your computer gets a virus, trojan, malware, hacked, or compromised in some other way.
Using a service like the WebCull bookmark manager can be a great mitigation against this because WebCull does not store your bookmarks on your hard drive like browsers do. Additionally, if you know your device has been compromised, you can access your account from a different device to change your password and cut other devices off from having access. This is not possible to do with browsers especially because of the local copies of the bookmark data.
![]()
Safari
✓ Safari sync has E2EE but you must enable the Advanced Data Protection system.
Safari syncs data via iCloud which is a robust system that encrypts many data types across Apple products. Not all of this data is encrypted with E2EE by default. Apple specifically states that bookmarks and many other data types are E2EE protected if you enable the Advanced Data Protection system for iCloud. Apple goes further to specifically state that your E2EE data cannot be seen by Apple and can only be decrypted on-device.
The Advanced Data Protection system is not enabled by default and is required to ensure that your data encryption key does not leave your device which is crucial to be considered E2EE. If you have not enabled it, your data is not protected with E2EE.
Encryption facts:
- If you choose to enable Advanced Data Protection, your trusted devices retain sole access to the encryption keys for the majority of your iCloud data, thereby protecting it using end-to-end encryption.
- No one else can access your end-to-end encrypted data — not even Apple
- End-to-end encrypted data can be decrypted only on your trusted devices
More from Apple:
- How to turn on Advanced Data Protection for iCloud
- We’re committed to protecting your data.
- iCloud data security overview
![]()
Microsoft Edge
Edge does not have E2EE sync and can decrypt your sync data server-side.
While Edge encrypts sync data in-transit and at-rest Microsoft has the ability to decrypt this data which is unsafe and does not qualify their sync system as E2EE. This means that although the data is secure during transmission, it is not entirely protected from potential access by Microsoft or potentially other entities like hackers attempting a data breach.
Edge does not claim to encrypt your data using an E2EE-like system which is very concerning. Only in their enterprise documentation do they address the issue, where they claim to not encrypt sync data on the client-side, which is very concerning. Their explanation is "to reduce resource utilization on end-user devices" which to us makes no sense and is not a valid or adequate explanation. Mind you this is the enterprise documentation and not the regular Edge documentation. The Edge documentation simply does not address the issue, so the enterprise documentation is all we have to go on and it's not looking great.
Encryption facts:
- Sync data is encrypted in transport using TLS 1.2 or greater.
- All data types are additionally encrypted at rest in Microsoft's service using AES128.
- Sync lacks client-side encryption and can be decrypted on the server-side.
More from Microsoft about Edge sync:
WebCull offers a robust solution for users concerned about the lack of end-to-end encryption (E2EE) in Microsoft Edge’s sync system. While Edge encrypts your data during transit and at rest, Microsoft seems to retain the ability to decrypt this data server-side, which compromises the overall security. WebCull steps in by providing true E2EE for your bookmarks, ensuring that your sync data is fully protected and only accessible to you. This means that with WebCull, you can safeguard your personal and sensitive information in a way that Edge’s current system cannot match, enhancing your privacy and security across all your devices.
Learn more about WebCull
![]()
Mozilla Firefox
✓ Firefox has an E2EE sync system, especially if you enable a primary password
Firefox sync appears to implement a type of encryption system similar to E2EE by default when creating your account. They never send your encryption key to the Mozilla servers, keeping it on your device, which is crucial for data privacy. They do this by using your Mozilla Firefox account password to encrypt your data being sent over the sync system. Firefox uses a one-way derived hashcode from your account password that is stored on your device to authenticate you on the sync server which returns your encrypted data. It sends your one-way encrypted key to the Mozilla sync server to be compared with a server-side copy. This is a pretty good design and fits the E2EE requirement.
This design is good but not perfect because your authentication key is derived from your decryption key. A one-way hash of your decryption key is sent to the Mozilla server when you sign up or change your password. This is less secure compared to if they never sent your decryption key as a one-way hash to the server because if ever someone figures out how to reverse the one-way hash back to the password, your data is now exposed. This would technically be a bit easier to compromise compared to decrypting your data directly. Even if an attacker was able to reverse the one-way hash to a million potential keys, this would be a huge advantage when it comes to a brute-force attack on your data.
Mozilla has implemented a high-quality (yet still not perfect) mitigation against this issue, but to benefit from it you must enable a primary password. Your primary password encrypts your passwords, thereby providing a client-side only password that is not one-way hashed and sent to the Mozilla sync server. This mitigation provides security that goes above and beyond the minimum criteria for an E2EE system. Yet, there still could be room for improvement in this design because it would be better if your data was not encrypted with your account password at all, even if it is encrypted by the primary password first. A better design would be if the data was encrypted directly with the primary password because it is not one-way hashed and sent to Mozilla at all.
Be aware that if ever you change your account password, or reset your primary sync password, you should be on a computer with a local version of your bookmarks. As highlighted by a comment on Mozilla support by Wesley Branton , this is because when you change your password, Mozilla doesn't know your previous password, and syncs whatever you have on your current device with your new password. So in some instances, this has meant people have lost their bookmarks without realizing that would happen when changing a Mozilla password using the "forgot password" feature.
You cannot have two different accounts in Firefox without merging their bookmarks, making it tough for multiple people sharing a computer, or people who simply want two different compartmentalized bookmark accounts. One solution is to rely on operating system profiles but this likely requires you to close all open applications which can be not user-friendly and time consuming. Another solution for someone in this situation is to consider using a different version of the browser like Firefox Developer Edition, Beta, or Nightly for different sync accounts.
Important takeaways from Firefox:
- The Primary Password feature encrypts passwords before storing them on your computer.
- Generating account recovery keys is crucial for account and data retrieval.
- Securing your data with Sync involves creating a unique password, which plays a crucial role in encrypting your data for complete privacy.
- Mozilla accounts uses your password to encrypt your data (such as bookmarks and passwords) for extra security
What could be improved:
It would be better if Firefox encrypted your data using your primary passphrase when you set it, rather than only encrypting your passwords with it. This is because your data is encrypted with your account password which has been one-way hashed and sent to Mozilla. This is a pretty good design but it could be better.
More from Mozilla about Firefox sync encryption:
- Using a Primary Password with Sync
- Use a Primary Password to protect stored logins and passwords
- Create a Primary Password
- The Future of Sync
- Private by Design: How we built Firefox Sync
![]()
Opera
Opera appears to have the features for an E2EE system but they are not working
Opera browser encrypts all sync data using your account password seemingly similar to how Firefox does it. They also appear to offer a personal passphrase option which is used to encrypt all your bookmarks but we can't get it to work. Account passwords are not a sufficient replacement for an E2EE passphrase because it is ideal that there is a key that never leaves the device. If the personal passphrase feature worked, we would potentially consider Opera as having an E2EE-like system.
At the time of writing this blog I could not get the Opera custom passphrase option to work. When I click the "Confirm your identity to enable encryption" it takes me back to my settings with nothing changed. I made a short video showing my issue and posted a question on reddit about it with the video, and tried again with another post, and I also contacted Opera support who I have not heard back from. I tried all the recommended tips to fix the issue but nothing is working. It could be a Mac-only thing, I have not tested it in Windows.
Encryption facts:
- By default, your passwords are encrypted using your Opera account credentials.
- Removing passwords from Opera’s password manager and your Opera account does not remove password data from your local machine.
- It appears that if you set a custom passphrase in Opera, the browser will encrypt all your sync data with it, which is an excellent design but unfortunately we could not get it working in the browser.
More from Opera about their sync system:
Sync Management Features:
WebCull provides an alternative for users who find Opera’s sync encryption system inadequate. Although Opera encrypts your sync data using your account password, which is similar to Firefox’s approach, this method falls short of true end-to-end encryption (E2EE). A key aspect of E2EE is that the encryption key should never leave the user’s device, something that Opera’s current system potentially does not guarantee. While Opera offers a custom passphrase option, which could potentially bring it closer to E2EE, this feature appears unreliable and difficult to activate.
With WebCull, you don’t have to rely on a system that may or may not work as advertised. WebCull ensures that your bookmarks are encrypted on your device before they are synced to the cloud, guaranteeing that only you can decrypt and access them. This level of security is what makes WebCull a reliable choice for privacy-conscious users, particularly when other browsers’ systems fall short of true end-to-end encryption. By using WebCull, you can rest assured that your bookmarks and other sensitive data remain under your control, no matter what device you are using.
Learn more about WebCull
![]()
Brave
✓ Brave has an E2EE sync system by default when turning on sync
Brave's sync system offers E2EE-like security by default. You do not have the ability to set a custom passphrase, instead the system generates a random phrase of words that appears to remain on-device. The phrase can be entered into other devices to create a sync chain that keeps all devices up-to-date with each other.
Encryption facts:
- Users who have a lot of browsing data (ex. 1000+ bookmarks) may experience a short delay before new data is displayed properly.
- Brave encrypts data at the client (device) level with encryption between each client in the sync chain, your data is hidden to Brave
- Brave leverages use of a 25th Sync code word to Sync a new device to the chain in addition to a QR code for easy scanning.
More from Brave about their sync system:
![]()
DuckDuckGo Browser
✓ DuckDuckGo has an E2EE sync system by default when turning on sync
Known for its focus on privacy, DuckDuckGo (DDG) browser provides an E2EE sync system. This ensures that user data remains private and secure, aligning with DuckDuckGo’s commitment to privacy.
DuckDuckGo uses a device-generated code to establish a key to encrypt and decrypt data using E2EE across devices. It is configured automatically when you enable sync across devices. It does not seem to offer the ability to change the key if needed. In the case of the device being compromised or stolen bookmarks would need to be deleted from the sync and re-added.
Important takeaways from DDG:
- Your data is encrypted from one end (the first device) to the other end (a second device) and is only readable in plain text from your devices that contain the encryption key.
- DDG does not have access to the encryption key and cannot read the data stored on our servers.
- Even if someone were to breach DDG servers and gain access to your data, it would remain encrypted, and they wouldn’t be able to read it without your encryption key.
More from DDG their sync encryption:
- DuckDuckGo Sync & Backup Privacy
- DuckDuckGo Smarter Encryption
- Learn About DuckDuckGo Sync Recovery Codes & Troubleshooting Tips
- How To Sync Favorites & Bookmark Icons Across Devices in DuckDuckGo
![]()
WebCull Sync Solution
What you can do if your browser doesn't have an E2EE sync system:
WebCull is a bookmark manager with a heavy focus on providing a quality, private bookmark sync system. It's an essential tool for anyone concerned with maintaining privacy in their online activities, particularly when it comes to managing browser bookmarks. While most modern browsers offer synchronization features, not all of them ensure that your data is protected through end-to-end encryption (E2EE). This means that your bookmarks, which often reveal a lot about your interests, intentions, and even sensitive personal matters, could be exposed to unauthorized access. This level of security is crucial considering data breaches and privacy violations are increasingly common.
Additionally, mainstream browsers store bookmarks in plaintext on your computer’s hard drive leaving your bookmarks accessible to other applications without special privileges and even when your browser is closed. WebCull provides a more secure alternative by keeping your bookmarks off your local device. This eliminates the risk of other applications accessing your data. That includes potential viruses, trojans, malware, getting hacked, or your device getting compromised in some other way. With WebCull, you mitigate this risk entirely. In the event of a security breach, you can quickly regain control by accessing your WebCull account from another device, changing your password, and cutting off access from the compromised device's. That is a level of security and control that traditional browsers simply can’t provide.
